Creating Azure Subscription
We need to visit Azure web site. There, you should click in “Start Free” and continue with the steps.
Now, we can sign in portal.azure.com.
Creating VM in Azure
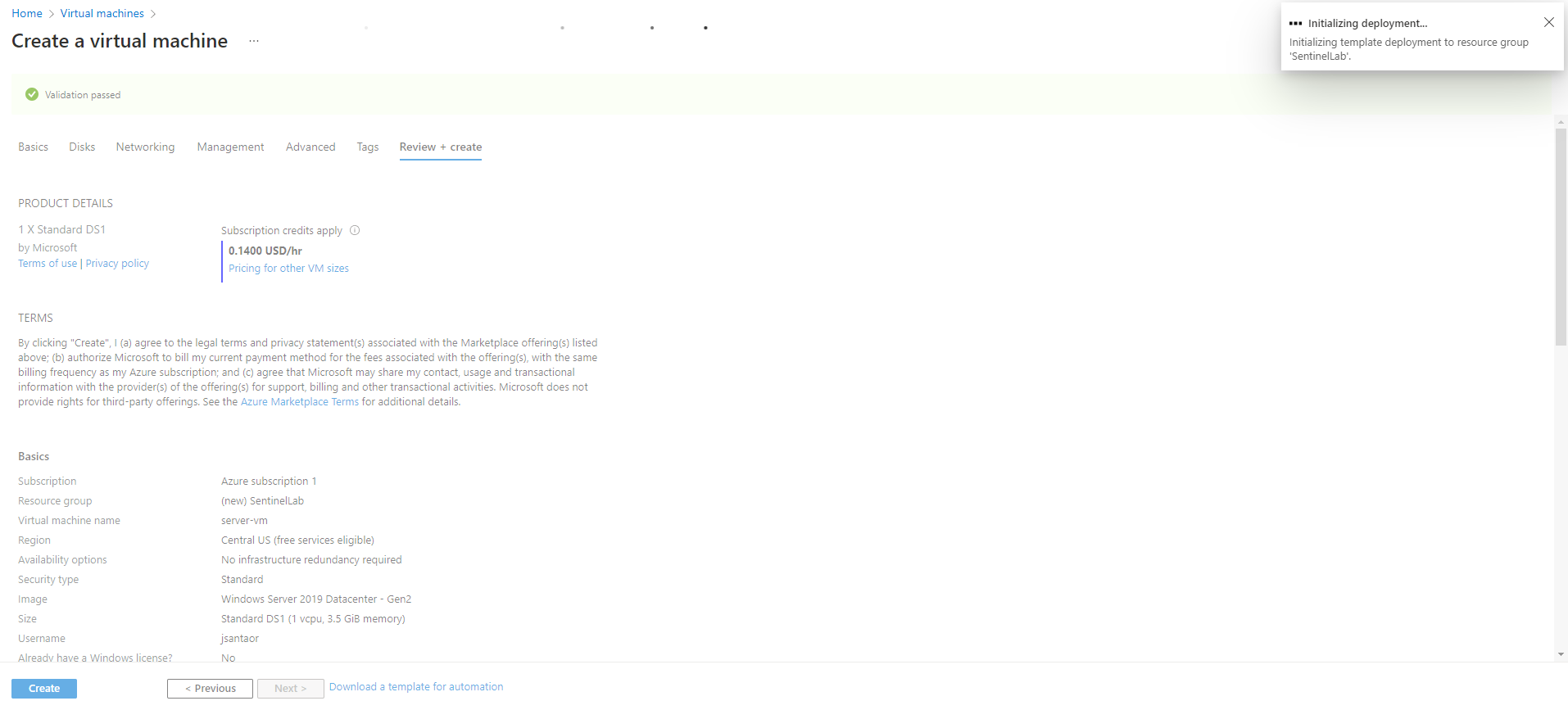
In order to create our VM, we click on “Virtual machines” option. Next, click in “Create” → “Azure virtual machine” with the following parameters:
- Resource group: create new → “SentinelLab”
- virtual machine name: server-vm
- Region: Central US
- user and pass
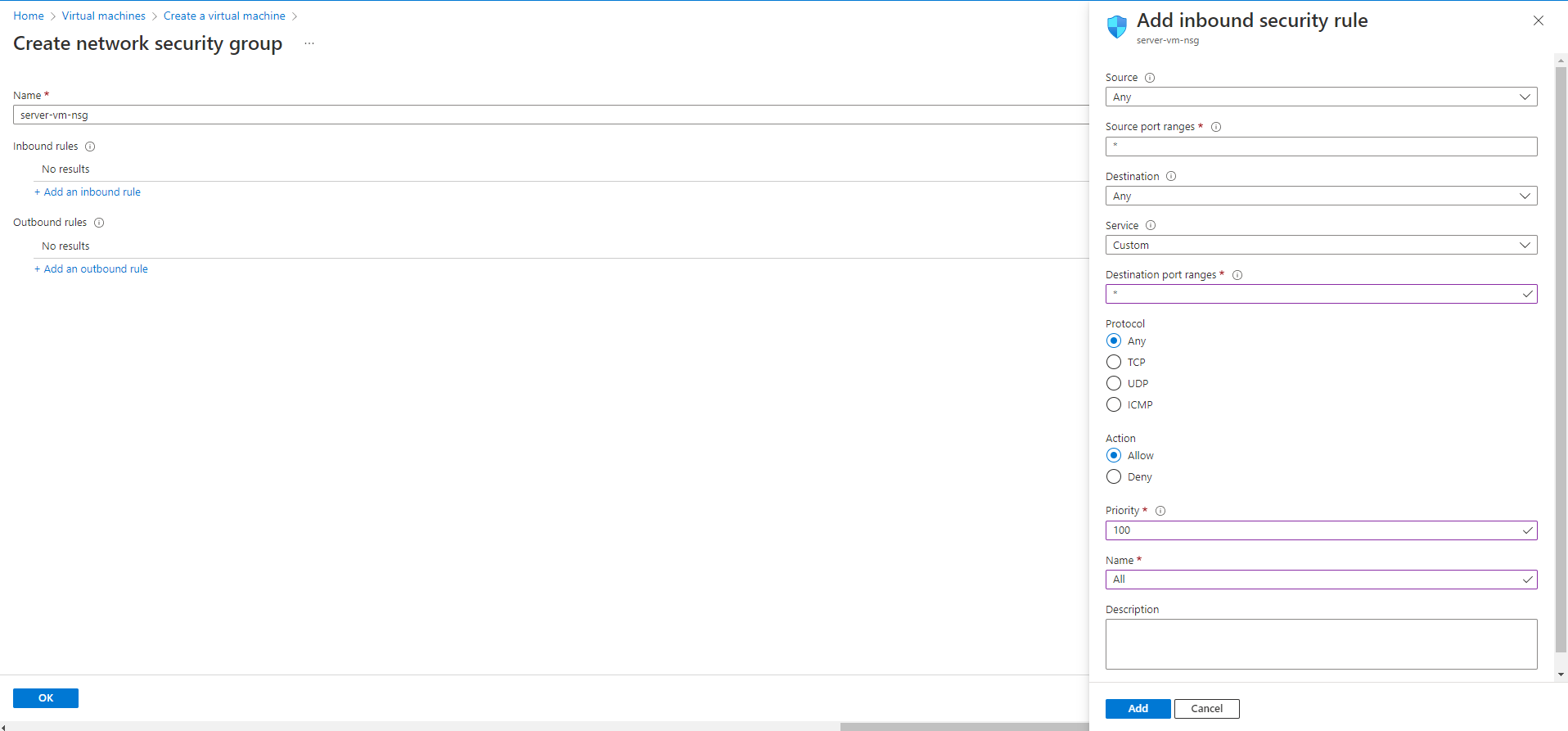
This server will serve as a vulnerable machine. Therefore, In the networking section, we are going to create a NSG (Network Security Group) which allows all traffic. The configurations is this:
- NIC network security group: advanced
- configure network security group: create new →
- create inbound rule: from any to any by all protocols with priority 100
NOTE: You shouldn’t do this in a real enrivonment.
Finally, click in “review+create”
when the VM is deployed, we should test our RDP. To do that, we can run “mstsc” and test our connection.
Creating a log analytics workspace
Now the goal is to ingest logs from the virtual machine. For that, it needs to create a log analytics workspace. here is a description of what log analytic is:
Log Analytics collects data from a variety of sources and uses a powerful query language to give you insights into the operation of your applications and resources. Use Azure Monitor to access the complete set of tools for monitoring all of your Azure resources.
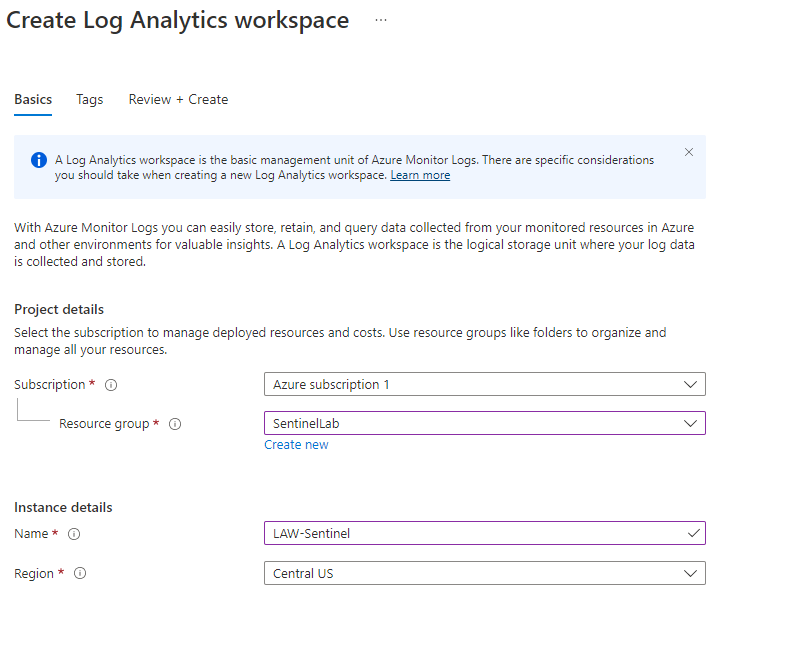
After, in the search bar we type log analytics workspaces → create log analytics workspace.
for this example, we select those parameters:
- resource group: the same of the VM
- name: LAW-Sentinel
- region: Central US
Finally, Sentinel will connect to this workspace in order to display the data
Enablig Microsoft Defender for Cloud
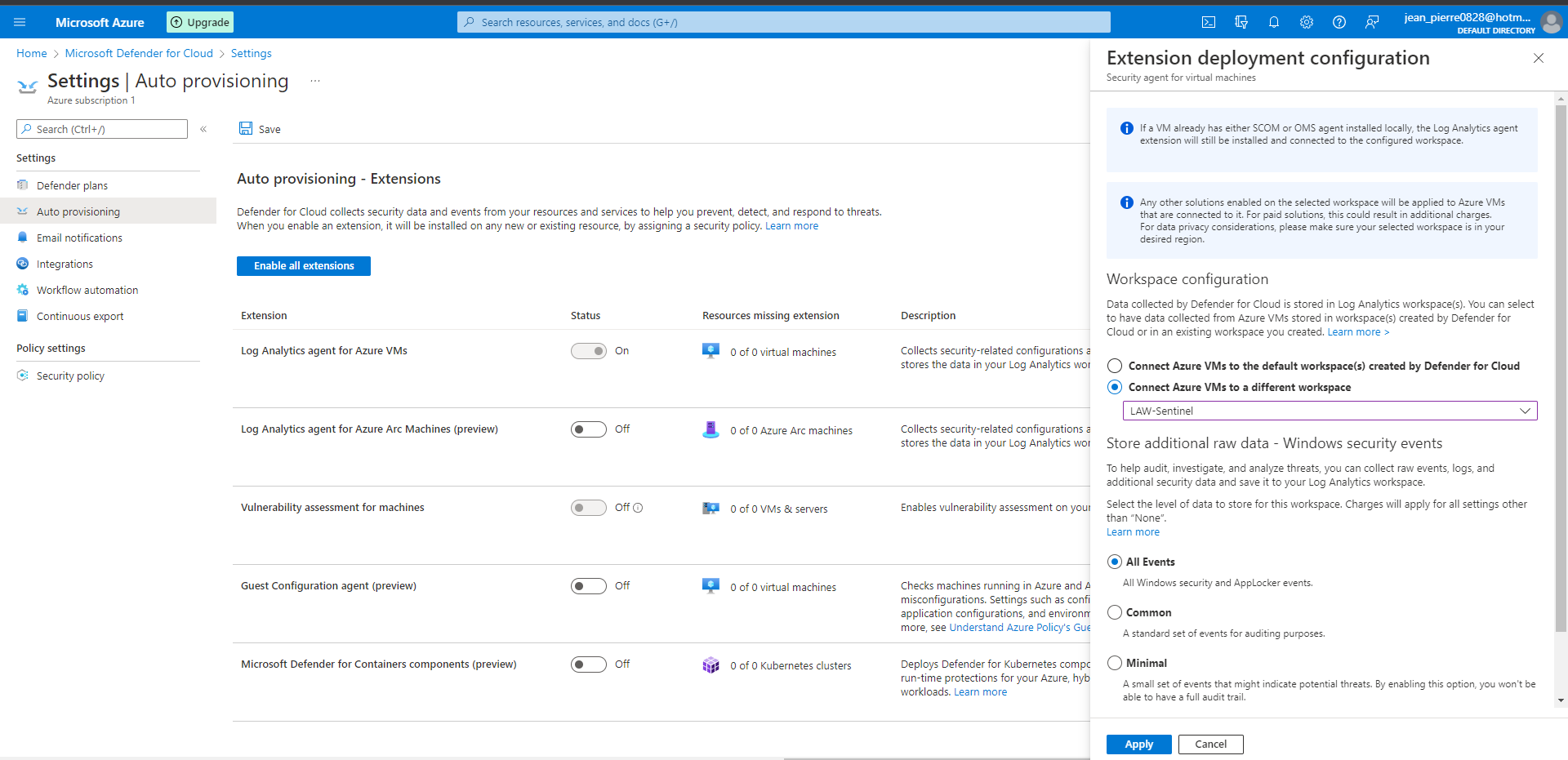
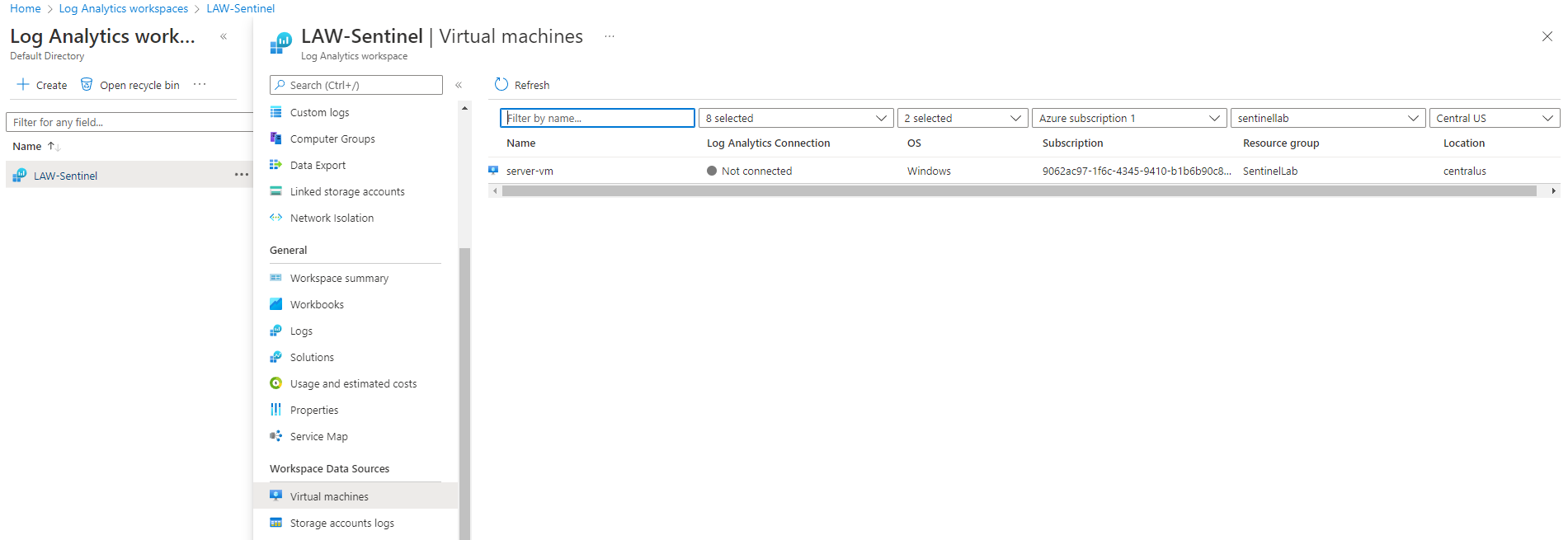
Now, it’s time to enable gather logs from VM into log analytics workspace. So, you need to search it and go to environment settings → select the subscription → auto provisioning → Log Analytics agent for Azure VMs to on → connect Azure VMs to a differente workspace: LAW-Sentinel
Afterward, we should back to the log analytics workspace to connect the VM
Note: the VM must be running to connect with the log analytics workspace
Set up Sentinel
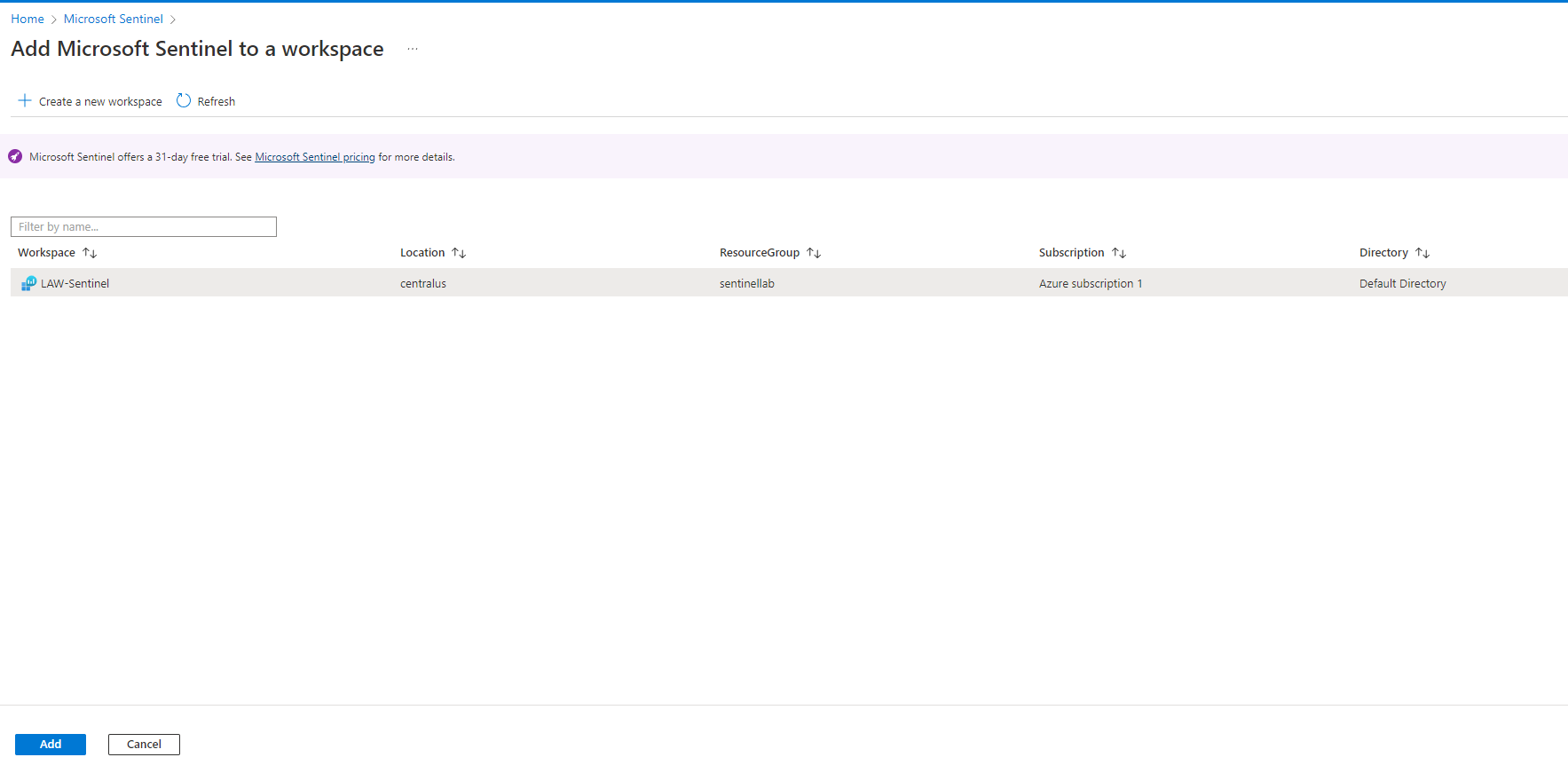
type Microsoft Sentinel in the search bar → create Microsoft Sentinel → select the workspace
we have a 30-day trial:
Microsoft Sentinel free trial activated: The free trial is active on this workspace from 26/4/2022 to 27/5/2022 at 23:59:59 UTC. During the trial, up to 10 GB/day are free for both Microsoft Sentinel and Log Analytics. Data beyond the 10 GB/day included quantity will be billed
Finally, we did a simple set up of Microsoft Sentinel and we can explore all features can give us Sentinel.